Resource administration module
The following sections provide information about the mechanisms for managing resources such as users, employees, or the organizational structure. Data access security in our system is also described.
Data confidentiality in the organization in the context of Action Audit
Data security is not only about preventing leaks outside the organization, but also about controlling the internal flow of information. The Action Audit application allows for convenient and comprehensive access management, enabling you to precisely define which user has access to what information.
Organizational structure
The organizational structure not only reflects the company’s shape in the Action Audit system but also affects a user’s access to specific resources. Assigning a user to an organizational cell in the structure determines the scope of accessible resources (e.g., action plans, audits, attachments, etc.), while roles determine the type of access.
The image below presents an example organizational structure of a manufacturing plant, with several departments highlighted. Additionally, the production department is divided into four audit areas.
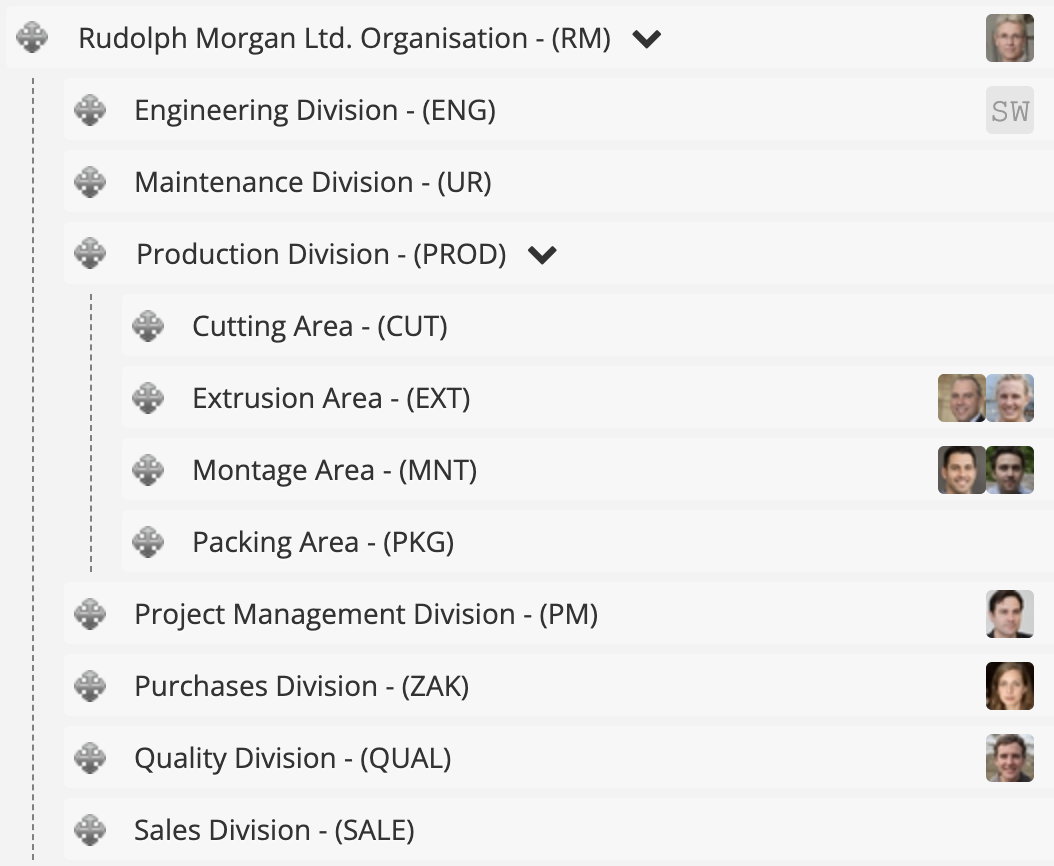
By assigning people to organizational cells, we ensure that the user will see data from their cell and all subordinate ones. For example, a person assigned to the top-level cell, Rudolph Morgan Sp. z o.o., will have access to data from the entire organization, while someone from the Assembly Area will only see data from that area.
The organizational structure determines what data a user can see, not what they can do with it.
Roles and permissions
Roles and their associated permissions define what operations a user can perform on the data accessible to them based on their position in the organizational structure. In simple terms, roles determine whether someone can view, edit, or delete objects such as audits, action plans, and activities.
Access to the action plan
This specification applies both to general action plans and similar objects such as audits, Kaizen ideas, potential incident events, and engineering changes. A user’s access to an action plan is influenced by:
-
Position in the organizational structure:
As described in the organizational structure section, a user has access to all objects assigned to their cell and subordinate cells. This assignment does not define whether the access is read-only or full access. -
Assignment as action plan owner:
A person designated as the action plan owner has full access to read and manage the action plan. -
Assignment to at least one activity as the responsible person:
Someone responsible for at least one activity in the plan can view the entire action plan, its structure, comments, attachments, and details of other users’ activities. This is because the person expected to complete the activity should understand the full context and have access to all related materials and information. -
Being the person responsible for a related resource, e.g., audit or Kaizen idea:
In Action Audit, two-step structures are available where the second step depends on conditions being met in the first. These include:- Audit and post-audit action plan – if the audit revealed at least one nonconformity
- Kaizen idea and implementation plan – if the idea was approved
- Potential incident and safety implementation plan – if the event was appropriately qualified
- Evaluation and implementation plan for an engineering change – if the change was justified
In such cases, the person responsible for the first step, such as the auditor, gains access to the resulting action plan, which is the second step. This rule also works in reverse.
-
Assignment as a participant, directly or via a user group:
Being assigned as a participant either directly or through a user group grants access to the action plan, regardless of structure or other conditions. -
Being the creator of the plan:
The creator initially gains access to the action plan. Upon creation, the person is assigned as a participant with write access. This gives them full rights to manage the plan but allows the possibility of removing that access later. A common case is when a department manager assigns someone to input the plan into the system, remaining as the plan’s owner. Then, the manager removes the creator’s access, retaining full control.
It is important to note that access to an action plan results from the sum of all the above factors. This means that meeting just one condition is enough to gain access to the resource.
Resource availability in the structure
The organizational structure has been described in the section above. It determines, among other things, which resources are visible to a user assigned to a given organizational unit within the structure.
The term “Resources” refers to the following elements:
- checklists
- audit areas
- audits
- action plans
- activities
- action plan templates
- attachments
- other users
Depending on where the user and the resources are assigned within the structure, there are two main types of access scope:
- from_structure – the user has access to resources assigned to their organizational unit and all subordinate units
- from_branch – in addition to the access described above, the user also has access to resources assigned to all units on the path between their unit and the root (usually the TOP unit)
Both scopes are illustrated in the following diagram:
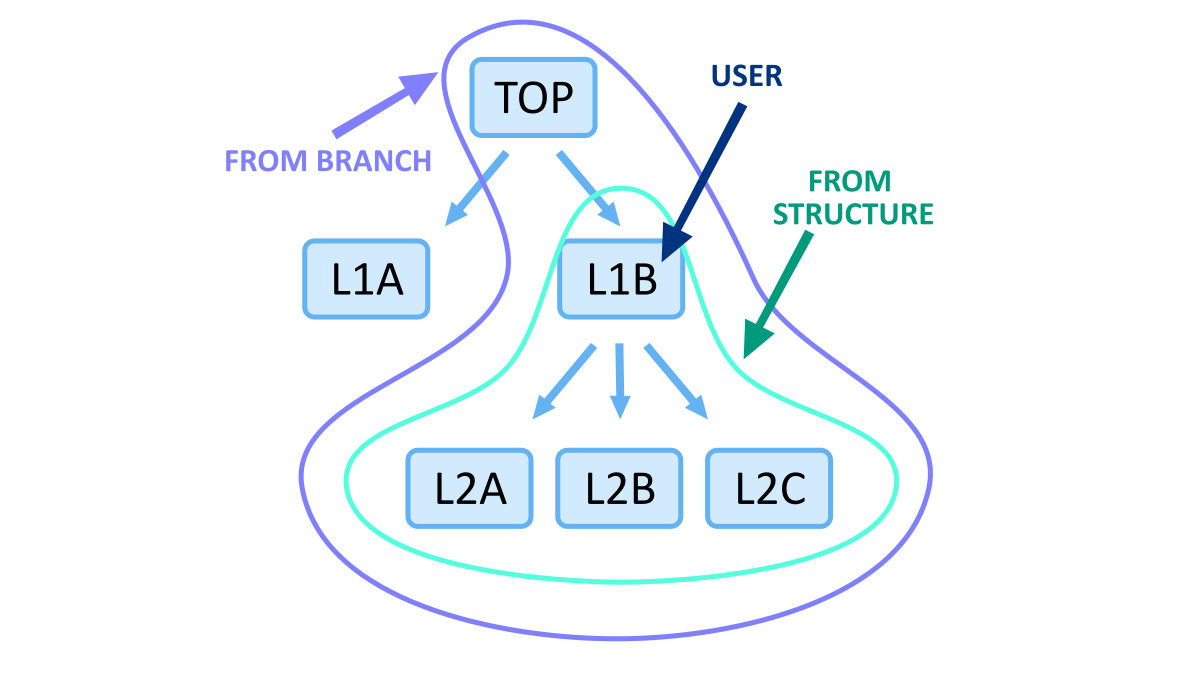
In the application, all resources are available to the user according to the from_structure access type, with two exceptions:
- Users – a user can see other users regardless of which organizational unit they belong to
- Checklists – a user can see checklists according to the from_branch access type
We are currently evaluating the possibility of changing the visibility scope of general templates from from_structure to from_branch. No decision has been made yet as to whether this change will be implemented.
Importing user and employee data
Action Audit allows for the import of various types of data from a spreadsheet using a file with the .xlsx extension. This enables fast data entry into the system without the need to manually input it through the application.
During the import process, users are matched by their email address. If you’re updating existing users, you can avoid creating duplicate accounts as long as the email address in the system and in the import sheet is the same.